Bucket Security Configuration
Each environment has a public and a private bucket configured. Access permissions to buckets can be assigned by adding credentials in the adapter or by setting permissions directly at the resource level.
Assigning permissions at the resource level
Resource-level permissions are assigned through a policy that must be assigned to the EC2 role where the container is executed. This policy can be assigned either to the adapter user or to the resource (for example, the EC2 container).
Policy Data
The policy must contain the following permissions (making sure to replace deyel and deyel-public with the correct bucket names):
{
'Version': '2012-10-17',
'Statement': [
{
'Sid': 'VisualEditor1',
'Effect': 'Allow',
'Action': 's3:ListBucket',
'Resource': [
'arn:aws:s3:::deyel ,
'arn:aws:s3:::deyel-public'
]
},
{
'Sid': 'VisualEditor0',
'Effect': 'Allow',
'Action': [
's3:GetObjectVersionTagging',
's3:GetStorageLensConfigurationTagging',
's3:GetObjectAcl',
'logs:CreateLogStream',
's3:GetIntelligentTieringConfiguration',
's3:GetObjectVersionAcl',
's3:DeleteObject',
's3:PutAccessPointPolicyForObjectLambda',
's3:GetObjectRetention',
's3:GetBucketWebsite',
's3:GetJobTagging',
's3:GetMultiRegionAccessPoint',
's3:GetObjectAttributes',
's3:GetObjectLegalHold',
'logs:CreateLogGroup',
's3:GetReplicationConfiguration',
's3:ListMultipartUploadParts',
's3:PutObject',
's3:GetObject',
's3:GetAnalyticsConfiguration',
's3:GetObjectVersionForReplication',
's3:GetAccessPointForObjectLambda',
's3:GetStorageLensDashboard',
's3:CreateAccessPoint',
's3:GetLifecycleConfiguration',
's3:GetInventoryConfiguration',
's3:GetBucketTagging',
's3:GetAccessPointPolicyForObjectLambda',
's3:ListBucketVersions',
's3:ListBucket',
's3:GetObjectVersionAttributes',
's3:GetBucketPolicy',
's3:GetEncryptionConfiguration',
's3:GetObjectVersionTorrent',
's3:GetBucketRequestPayment',
's3:GetAccessPointPolicyStatus',
's3:GetObjectTagging',
's3:GetMetricsConfiguration',
's3:PutObjectAcl',
's3:GetBucketPublicAccessBlock',
's3:GetMultiRegionAccessPointPolicyStatus',
's3:ListBucketMultipartUploads',
's3:GetMultiRegionAccessPointPolicy',
's3:GetAccessPointPolicyStatusForObjectLambda',
's3:GetBucketVersioning',
's3:GetBucketAcl',
's3:GetAccessPointConfigurationForObjectLambda',
'logs:PutLogEvents',
's3:GetObjectTorrent',
's3:GetStorageLensConfiguration',
's3:CreateAccessPointForObjectLambda',
's3:GetBucketLocation',
's3:GetAccessPointPolicy',
's3:GetObjectVersion'
],
'Resource': [
'arn:aws:s3:::deyel/*',
'arn:aws:s3:::deyel-public/*'
]
}
]
}
CORS Configuration for Buckets
Buckets must be configured appropriately to allow or deny public access, as appropriate.
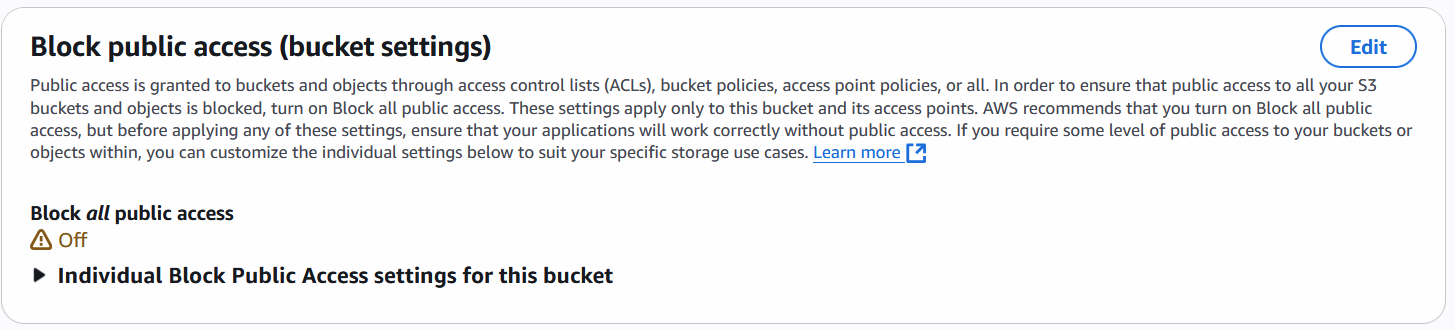
Public bucket configuration
Block all public access: OFF, (Block all public access = OFF)
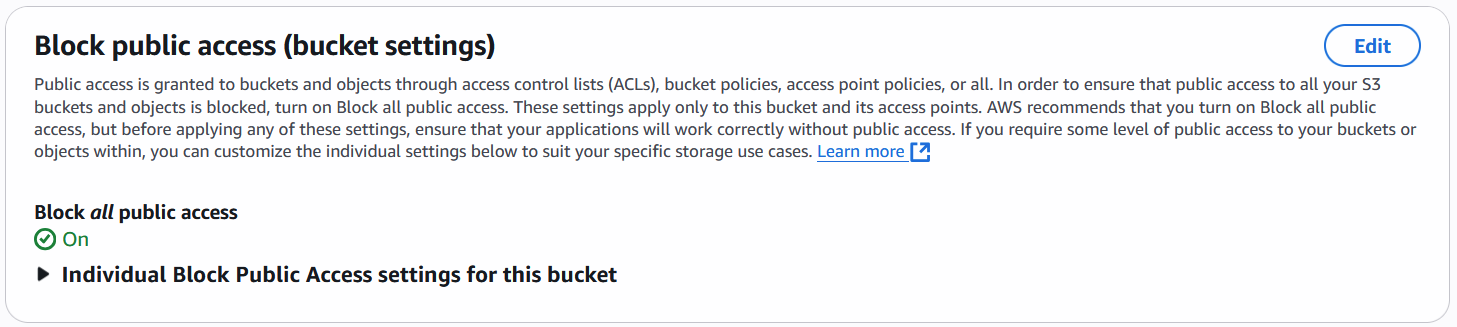
Private bucket configuration
Block all public access: ON, (Block all public access = ON)
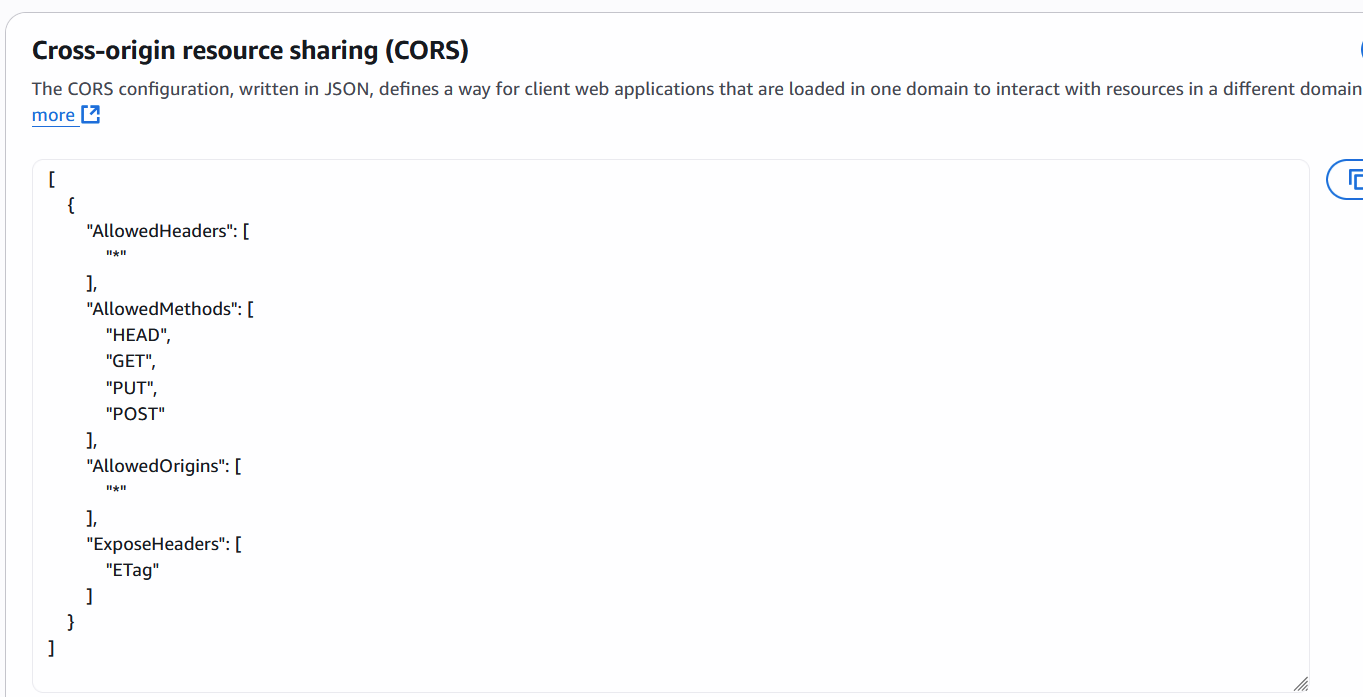
CORS Configuration
In the permissions section, enable the Cross-Origin Resource Sharing (CORS) option and configure the following methods:
[
{
'AllowedHeaders': [
'*'
],
'AllowedMethods': [
'HEAD',
'GET',
'PUT',
'POST'
],
'AllowedOrigins': [
'*'
],
'ExposeHeaders': [
'ETag'
]
}
]